News

Cybersecurity
Take necessary precautions to protect your data and review the IT Acceptable Use Policy. Due to the rise in online presence and remote work, phishing and other scams are on the rise. To improve your security, review online security and data security best practices. The UIS Security website contains further useful material on cybersecurity.
Restarting your computer once a week helps to clear random, unimportant temporary files that slow down the device. Please note that closing your laptop is not the same as restarting it or shutting it down.
Please consider the tips below to improve the security of your personal devices.
Installing the latest computer and software updates keep your devices running smoothly and securely. Faculty and staff are issued with GU-Q issued devices and software updates are deployed automatically. Instructions for updating personal devices with various operating systems and software applications can be found below:
Sign in to the Zoom application. Click your profile picture in the top right corner of the Zoom application then click Check for Updates. If there is a newer version, Zoom will download and install it.
Chrome
On a PC: Click on the Customize and Control Google Chrome icon (the three dots in the upper right-hand corner of the window), choose Help>>About Google Chrome. Chrome will automatically install updates.
On a Mac: Click on the About Google Chrome in the drop-down menu under Chrome on the toolbar (at the top left of your screen next to the Apple), to search for updates.
Updating Windows 10 or 11
Click on the Windows Start button in the taskbar, choose Settings>>Update & Security>>Windows Update and then select Check for Updates. If updates are available, they will appear on the Windows Update page. To install them, select Download and Install Now.
Updating Mac OS
Click on the Apple icon in the upper left-hand corner of your screen, choose About This Mac from the drop-down menu, and then click the Software Update button in the pop-up window. In the ‘Software Update’ window, click the Update Now button to install the available updates.
Microsoft Office on a PC
You can turn on the option to receive Microsoft Office updates by following these instructions.
Microsoft Office on a Mac
Open Microsoft Word and select Help > Check for Updates. Older versions may not automatically update.

Cisco Webex Telephone Software
Dear Faculty, and Staff,
Webex will provide faculty and staff with additional flexibility to make and receive calls directly from PC, laptop, or mobile device, complementing our existing desk phone setup. You will be able to use Webex on multiple devices, enabling you to stay connected seamlessly wherever you are, if you choose to.
Our IT staff will be reaching out soon to schedule individual appointments (onboarding session) for setup. During these appointments, we will install the software, provide training, issue a USB headset to ensure a smooth transition and guide you through the basics of using Webex Calling, setup Webex on your device and answer any questions you may have.

Zoom AI Companion
The Zoom AI Companion feature has now been successfully made available to GU-Q staff. If faculty would like IT to activate this feature on their Zoom account then please email us at guqhelpcenter@georgetown.edu.
Further details regarding Zoom AI Companion, including good practices and data security information, are provided below.
In your Zoom meetings, it can:
- Summarize Zoom meetings, denoting what happened and action items, even without recording the meeting.
- Answer questions you have about a meeting in real-time, such as:
o Was my name mentioned?
o What are our next steps?
o What did I miss? Can you catch me up?
o What did [person] say about [topic]?
- Make recordings easier to review by dividing them into smart chapters by topic, highlighting important info and identifying action items.
Get Started with Zoom AI Companion:
We have developed a Zoom AI Companion site for answers to the most common questions about getting started. You can also visit Zoom’s support page: Using Zoom AI Companion.
You can find the AI Companion sparkle icon while you’re in a Zoom Meeting on the bottom toolbar to see what’s currently active.
To turn off specific AI Companion capabilities, go to your Zoom profile settings in a web browser and look for the AI Companion tab.
Zoom AI Companion and Data Security:
You control which AI Companion capabilities you want to use in meetings you host.
- Only a meeting host or co-host can activate the Zoom AI companion for a meeting.
- Meeting hosts must inform participants that Zoom AI Companion will be used during a meeting and ask if there are any concerns or questions. Please ensure all meeting participants are comfortable with you using the new tool. See below for recommendations for informing participants.
- Meeting participants will receive a message that Zoom AI Companion has been turned on for a meeting.
- You can turn these capabilities on or off at any time and choose whether or not to use them in your meetings on a case-by-case basis.
- You can also choose when to turn AI Companion on or off during your meeting.
- A glowing sparkle icon will be visible in the top-left corner of your window if the AI Companion is active during a meeting.
- If you join a meeting where AI Companion capabilities are being used, you’ll see a notification describing the active capabilities for that meeting.
Zoom AI Companion is similar to recording tools that are already available to hosts which include video recording meetings and generating a meeting transcript.

Important Alert: Rise in Bank Fraud Cyberattacks
Increasingly, there are cyberattacks including phishing attempts aimed at stealing personal information, and efforts to install malicious software (malware) on electronic devices.
Cyberattacks can lead to serious consequences, including data breaches, disruptions to academic and administrative operations, and personal financial loss.
To help safeguard yourself and our community, please take a moment to review the following tips for identifying cyber threats and adopting best practices:
- Banking frauds: The bank will not ask for personal information via phone. If you get a call or message from someone claiming to be your bank, go to a branch or call the phone number on the back of your bank card to confirm it is a valid request.
- One-Time Passcodes (OTP): Never share your OTP with anyone. Always confirm that you personally initiated the request that generated the OTP and that you entered it yourself for any purchase. Remember, once you share your OTP, your money may be at risk.
- Unsolicited communications: Be wary of unsolicited emails, calls, or text messages from unknown senders, particularly those requesting sensitive information or urging immediate action.
- Sender identities: Before responding to any communication, carefully verify the sender’s identity and authenticity. Look for signs of suspicious activity, such as unfamiliar email addresses or phone numbers.
- Sensitive information: Refrain from sharing sensitive information such as passwords, financial details, or personal ID numbers (e.g. QID or US Social Security) via email or text messages. If it is absolutely necessary to share this type of information, use a secure channel after verifying recipient identity.
For more comprehensive information on cybersecurity, how to safeguard Georgetown data, and personal security measures, please click here. By staying informed and adhering to best practices, we can collectively strengthen our cybersecurity posture and safeguard against potential threats.
For additional support and guidance
Students: Please contact John Wright, Director of Student Life (email: jcw57@georgetown.edu | Office 1F11).
Faculty and Faculty: Please contact Omar Al Swadi (email oma6@georgetown.edu | Office 1A47).
To report an IT incident, please contact guqhelpcenter@georgetown.edu or 4457 8130.
Thank you and stay safe online!

Phishing Alert!
Recently, there has been an increase in phishing emails and text messages, used to conduct fraudulent activities to deceive individuals into disclosing sensitive information.
Phishing is a form of fraud in which a scammer’s message (email /chat /text /call) attempts to trick the recipient into divulging important personal information like a password or bank account number, transferring money to assist in financial fraud, or installing malicious software. Usually, the sender pretends to represent a legitimate organization, such as a university leader, bank manager/staff, senior executive, institutional department, governmental agency, or employee.
How to report a suspicious email?
To help combat phishing attacks and better protect personal and university data and reputation, your Georgetown email accounts have access to the Cofense Phishing Reporter tool as an add-on to the Georgetown University Google email interface. The Cofense Reporter add-on appears as a fish icon on the right-hand side toolbar of your Gmail screen.
“When in doubt, click the trout.”
If you receive a suspicious email, simply click the Cofense Reporter button (the fish icon) to inform Georgetown’s University Information Security Officer (UISO). The fish icon encourages users to remember “When in doubt, click the trout.”
Tips to catch fraudulent cyber scams:
- Exercise caution with unsolicited communications: Be wary of unsolicited emails, calls, or text messages from unknown senders, particularly those requesting sensitive information or urging immediate action.
- Verify sender identities: Before responding to any communication, carefully verify the sender’s identity and authenticity. Look for signs of suspicious activity, such as unfamiliar email addresses or phone numbers.
- Beware of urgent requests: Exercise caution when receiving urgent requests for personal information, financial transactions, or account credentials. Cybercriminals often use urgency as a tactic to pressure individuals into making hasty decisions.
- Scrutinize URLs and links: Take extra care when clicking on links embedded in emails or text messages. Hover your cursor over the link to preview the URL and ensure it directs to a legitimate and secure website.
- Avoid sharing sensitive information: Refrain from sharing sensitive information such as passwords, US social security numbers, Qatari identification numbers, or financial details via email or text messages or calls, unless absolutely necessary and only share sensitive information through secure channels after verifying recipient identity.
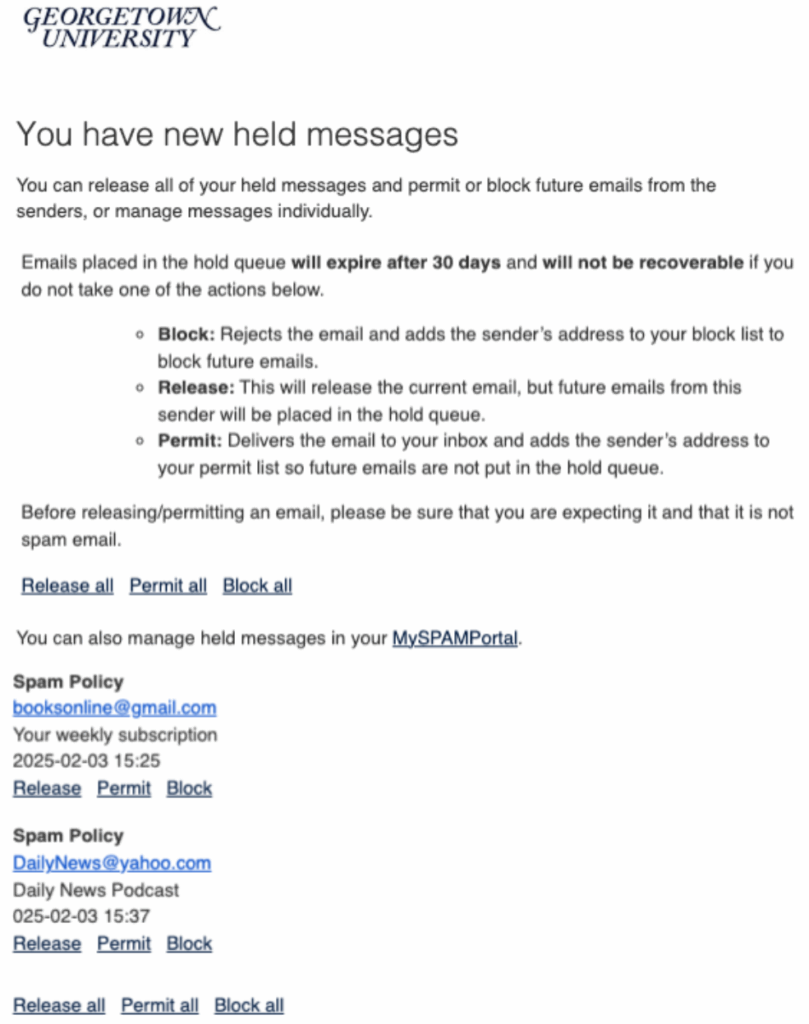
New Email Security Filter
In order to further enhance protection against phishing, fraudulent, and malicious content, the university security office has deployed a new service providing additional email security. An added benefit to this additional protection is that you will be able to manage and reduce unwanted emails, like spam and junk.
As a result of this change, the only one noticible difference you will notice is receiving two daily digest emails daily titled, “You have new held spam messages,”, at 10 a.m. and 5 p.m Doha time. If you have no new spam emails, you will not receive this notification.
You can also manage held emails by logging in to the held email location (i.e., the MySPAMPortal) using your NetID@georgetown.edu email address and NetID password.
Thank you for your participation in this effort to enhance cybersecurity at Georgetown. For more information, please read the FAQ on the UIS website.